To detect the Petya attack in the infrastructure, the following indicators can be used:
C:\Windows\perfс
A task in Windows Scheduler with an empty name and action (reboot) "%WINDIR%\system32\shutdown.exe /r /f"
IDS/IPS rule triggers:
msg: "[PT Open] Unimplemented Trans2 Sub-Command code. Possible ETERNALBLUE (WannaCry, Petya) tool"; sid: 10001254; rev: 2;
msg: "[PT Open] ETERNALBLUE (WannaCry, Petya) SMB MS Windows RCE"; sid: 10001255; rev: 3;
msg: "[PT Open] Trans2 Sub-Command 0x0E. Likely ETERNALBLUE (WannaCry, Petya) tool"; sid: 10001256; rev: 2;
msg: "[PT Open] Petya ransomware perfc.dat component"; sid: 10001443; rev: 1
msg:"[PT Open] SMB2 Create PSEXESVC.EXE"; sid: 10001444; rev:1
Signatures::
https://github.com/ptresearch/AttackDetection/blob/master/eternalblue(WannaCry%2CPetya)/eternalblue(WannaCry%2CPetya).rules
Petya use the TCP ports 135, 139, 445 atraves dos serviços SMB e WMI.
How to active the Kill-switch?
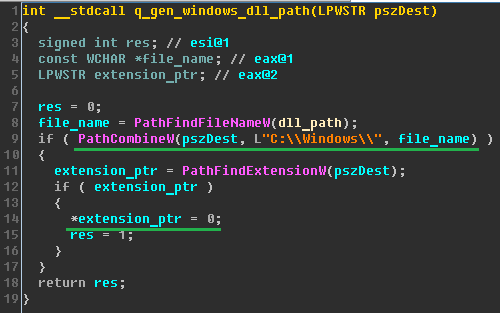
Petya checks if the perfc file exists in the "C:\Windows" the directory and the drive is hardcoded. The perfc file has no content is just an empty file without extension and only with read permissions.
 |
| Source: www.ptsecurity.com |
No comments:
Post a Comment